Explain Different Types of Computer Criminals
Move documentary evidence quickly from the printed or typewritten page to computer data stored on floppy diskettes Zip disks CDs and computer hard disk drives. An example of a DDoS attack.

How Have Digital And Social Media Impacted Cyber Crime And Internet Forensics Infographic Forensics Social Media Impact Criminal Psychology
Therefore it is about time that you be cognizant of the different types of cybercrimes.

. Copyright violation - Stealing or using another persons Copyrighted material without permission. This category of cybercrime involves one individual distributing malicious or illegal information online. Cyber Criminals and its types 1.
Cyber criminals pretending to be someone else can trick unsuspecting employees to compromise data. Below is a list of the different types of computer crimes today. The term hacker may refer to anyone with technical skills however it typically refers to an individual who.
Spamming wherever outlawed completely or where regulations controlling it are violated. It works exactly the way fishing trap does where are trapper. In order to protect yourself you need to know about the different ways in which your computer can be compromised and your privacy infringed.
Checklist of Types of Computer Forensics Technology. Unauthorised access to or modification of o programs see software cracking and hacking. Clicking any of the links gives further information about each crime.
All the different Types of Cyber Crimes Explained 1. This is the least common cybercrime but. Create a new type of virtual evidence for e-commerce transactions and email communications over the Internet.
Examples of computer crime are. Usually work anonymously and create tools. These criminals embody organizations of cyber criminals hacktivists terrorists and.
While there are four primary types of computer crimes multiple crimes can occur during any given criminal transaction. 1 The Social Engineer. Crimes that use computer networks or devices to advance other ends include.
Zombie Computer a computer which is deliberately hacked by cyber criminals in order to gain access to andor attack a private network. The typical script kiddie finds and exploits holes in interne View the full answer. Distributed Denial of Service DDoS with a DDoS attack cyber criminals are not necessarily seeking to access data but rather are hoping to shut down a network via an overload of junk data.
SIX 6 different types and characteristics of common computer criminals. Criminal hacking is the act of gaining unauthorized access. Someone who wants to be a hacker or thinks they are but lacks any serious.
In all of these crimes the offender uses the computer to obtain information or to. This type of cybercrime takes place when a person uses personal information or of another. Discount pharmaceuticals time-shares personal ads from.
Identify theft is a specific form of fraud in which cybercriminals steal personal data including passwords data about the bank account credit cards debit cards social security and other sensitive information. The word phishing is re-spelling of fishing. Fraud and identity theft although this increasingly uses malware hacking or phishing making it an example of both computer as target and computer as tool crime Information warfare.
Types of Computer-Based on Types. Previous question Next question. These phenomena may be such as electrical mechanical or hydraulic quantities and they are.
The three types of computers along with their functions are given below. Here are some common threats and steps a business can take. Heres the list of cybercrimes that have at times brought the most prepared of all nations down to their knees.
Deliberate circumvention of computer security systems. Computer crimes that can get you into serious trouble In todays world much of the criminal activity occurs not in the streets but behind a computer screen. Your email inbox is probably full of their work.
Criminals who infiltrate computers and networks have developed a variety of malicious software and social engineering techniques used individually or in combination when use in committing different types of cyber crime. What are the Common Types of Cyber Crimes. Script kiddies Scammers Hacker groups Phishers Insiders Advanced Persistent Threat APT Agents Script kiddies.
This can include cyberstalking distributing pornography and trafficking. View the full answer. A Viruses and Malware-Viruses and malware that can be dangerous to your computer.
Hacking is the act of breaking into a computer without the users knowledge or permission. Ans-There are four types of computer crimes. In one scenario a spoof email purporting to be from the CEO.
Analog Computer An analog computer one that uses the continuously changeable aspects of physical phenomena to model the problem being solved. Child pornography - Making distributing storing or viewing child pornography. 1 Script kiddies.
In other words crime and legality are social constructs that are fluid and change over time. Through identity theft criminals can steal money. There are different types of hacking methods and procedures.
A few of the most common cyber crimes are described below. The 12 types of Cyber Crime. Fraud achieved by the manipulation of computer records.
Many crimes now occur from afar with the authorities putting the pieces together with forensic analysis to retrace criminals steps. Brute-Force and Dictionary Network Attacks. Crimes in which the computer is the target include the theft of intellectual property or marketing information blackmail or sabotage of operating systems and programs.
A crime is defined as any act that is contrary to legal code or laws. There are many different types of crimes from crimes against persons to victimless crimes and violent crimes to white collar crimes. Understanding the types of cyber criminals and their techniques can help protect your organization from a data breach.

Types Of Cybercrime Panda Security Mediacenter

Types Of Cybercrime Panda Security Mediacenter

The A To Z Of Malware Infographic Blog Bullguard Your Online Security Hub Malware Learn Hacking Infographic

The Basics Of Cyber Security Visual Ly Cyber Security Technology Computer Security Cyber Security Awareness

Types Of Cybercrime Panda Security Mediacenter

Uk Small Business Twitter Search Cyber Security Cybersecurity Infographic Business Communication
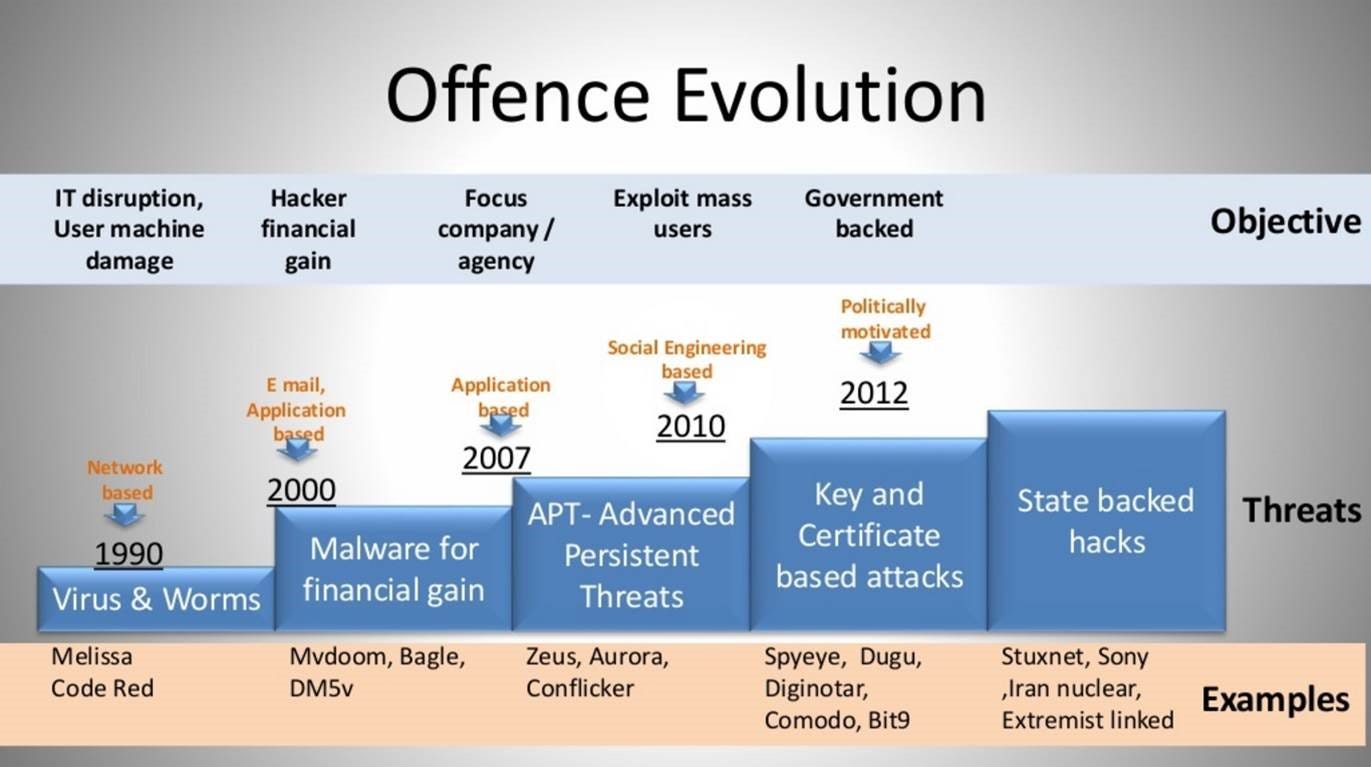
Cyber Crime Categories And Types The Growth And Progress Of Digital By Ensar Seker Digital Diplomacy Medium

Inside The Mind Of A Cybercriminal

Cybercriminals An Overview Sciencedirect Topics

Cyber Crime The First One Question That Is Ears In Over Mind What Is Cyber Crime Answer Is So Simple All The Computer Related Crime Is Done Online Or Off Line

Who Are Cyber Criminals Norwich University Online

Cybercrime Which Ones Are The Most Common Threats Today Red Points
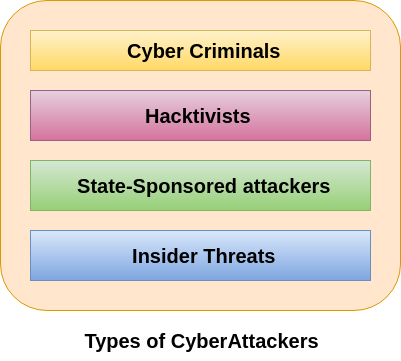
Types Of Cyber Attackers Javatpoint
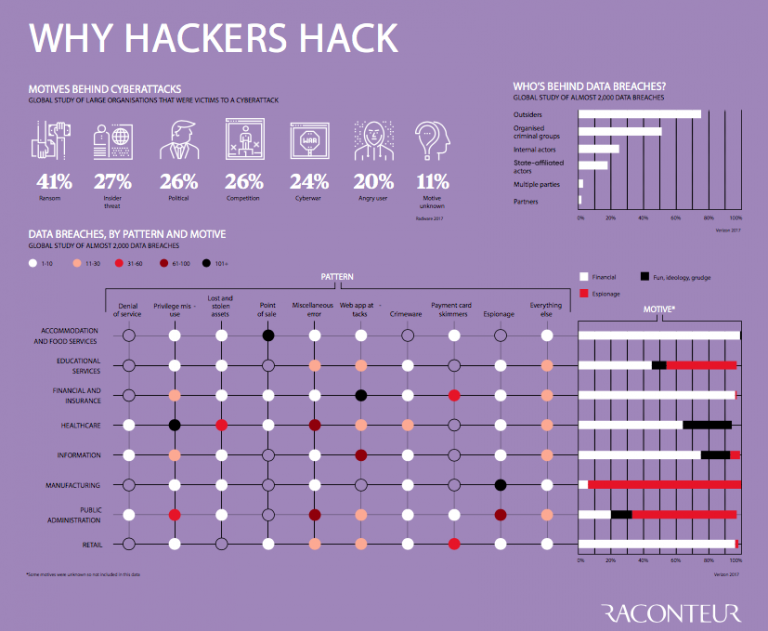
Cyber Criminals Who They Are And Why They Do It

Cyber Crime Types Examples And What Your Business Can Do

Cyber Security Importance Types And Best Practices Micronova It Solutions Cyber Security What Is Cyber Security Cyber Security Threats
Cyber Crime Categories And Types The Growth And Progress Of Digital By Ensar Seker Digital Diplomacy Medium

7 Types Of Cyber Crimes And Criminals Faronics

Who Are The Targets In Today S Cyber War Zone Infographic Cyber Security Awareness Cyber Infographic